What Is A Multi Factor Authentication
Nowadays, a lot of companies are offering the options of hybrid and online working days alongside going to the office to their employees. To make the transition between different types of jobs easier for them, most companies started to store a lot of their confidential data on online platforms and communicate with their customers online as well.
The increase in the amount of data available online has increased the possibility of being subjected to cyber attacks from those outside of an organization. For that reason, many organizations have found that only using a username and a password is not enough protection – thus, they started to search for other layers of protection.
One of the ways to protect company accounts is through Multi-factor authentication (MFA) applications. When an MFA is connected to an account, those who are trying to log in need to verify their identities to access their accounts.
What Is Cisco Anyconnect And The Importance Of Securing It
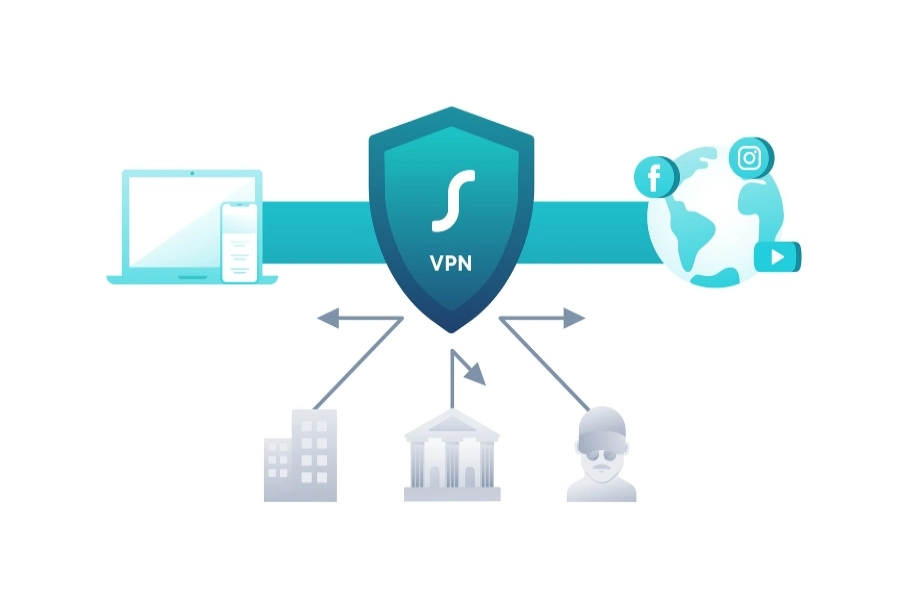
Many organizations find that only securing company accounts is not enough. For that, a lot of companies have leaned towards using Virtual Private Networks (VPN), such as the Cisco Anyconnect. These VPNs provide a firewall between devices – no external device can access the storage of company devices. However, it is important that businesses add MFA protections to their VPN accounts as well.
For example, businesses that have connected a Cisco Anyconnect Multi Factor Authentication are free of outside threats and have reduced their chances of getting hacked, alongside decreasing their internet access’s vulnerability.
So, businesses gain major benefits when they connect their VPN accounts to multi factor authentications. Some other benefits include identifying phishing links by not directing users to the hacker’s link and informing business accounts when a brute force attack is being made on their accounts.
Thus, it is important for businesses to add another layer of protection to their VPN applications to enjoy the benefits that come with it.
Steps To Follow To Secure The Cisco Anyconnect VPN Of A Business
If you are connecting an MFA provider for your company’s VPN account, here are some steps that could help make the process easier.
1. Finding the most appropriate MFA application
First and foremost, it is important that managers dedicate time and effort to finding the best practical MFA application for their corporate culture. There could be that some MFA applications work on a more complex level than others and require additional skills from the users to operate. For that, managers need to identify the complexity level best fit for their corporate culture.
After finding the MFA application, download the up-to-date version of it to enjoy its benefits.
2. Creating a company username and password on the MFA application
Now that the application is installed, managers need to create an admin account in the MFA application. This admin account is the domain to which all company accounts will be connected to. In other words, the admin account has access to what account they can give access to company data.
For some MFA applications, users need to submit an application form for the admin account, and once they receive the approval, they can move to the next step.
3. Connecting the MFA to Cisco VPN
By using the admin accounts’ username and password, log into the MFA application, and you’ll see a place where you need to include your company’s VPN link. The link might be in this form “http//vpn.corporationname.com/”
4. Choosing the type of the second authentication
Now that the VPN and MFA applications are connected, there are numerous options to choose which type of multi-factor authentication to use. The most common types are fingerprint scans, face recognition, and one-time code sent to a mobile phone. These options ensure that the user is from a certain organization and gives them access to the organization’s data.
5. Logging in and getting access to the account to ensure that no one other than you can access your Cisco account
Log into your VPN account and test whether the MFA is working properly so that the organization’s VPN will be protected with the extra layers.
Conclusion
To conclude, usernames and passwords nowadays are not enough to protect online platforms and company data. For that, it is crucial to connect an MFA application to communication platforms, cloud storages, and even VPN applications.